30% Of Internet Users Admit To Buying From Spam : ugh. we need a reminder of the Boulder Pledge. Mind you, Marshal have put out what appear to be inaccurate figures in the past regarding the Rustock botnet, so apply a pinch of salt
(tags: marshal spam boulder-pledge commerce shopping statistics via:techdirt)more details on EC2 Elastic Block Store : achieves 70MB/s on an m1.small instance; ‘performance exceeds what we’ve seen for filesystems striped across the four local drives of x-large instances’. pretty good for a network filesystem, although not great compared to fast local SATA disks. also: snapshots are incremental and perform nicely compared to local S3 copy-and-upload
(tags: ebs amazon performance benchmarks s3 ec2 disks snapshotting filesystems)Amazon Elastic Block Store (EBS) : ‘Prior to Amazon EBS, block storage within an Amazon EC2 instance was tied to the instance itself so that when the instance was terminated, the data within the instance was lost. Now with Amazon EBS, users can chose to allocate storage volumes that persist reliably and independently from Amazon EC2 instances.’ — can even snapshot to S3
(tags: amazon ebs ec2 aws s3 cloud-computing hosting)
Justin's Linklog Posts
Here’s my results for <a href="http://www.verygoodtaste.co.uk/uncategorised/the-omnivores-hundred/”>The Omnivore’s Hundred, a silly foodie "purity test". Bold are items I’ve eaten; crossed-out items are ones I wouldn’t eat again. I score 70 out of 100, and clearly need to eat less Asian and more European cuisine ;)
- Venison
- Nettle tea
- Huevos rancheros
- Steak tartare
- Crocodile
- Black pudding
- Cheese fondue
- Carp
- Borscht
- Baba ghanoush
- Calamari
- Pho
- PB&J sandwich
- Aloo gobi
- Hot dog from a street cart
- Epoisses
- Black truffle
- Fruit wine made from something other than grapes
- Steamed pork buns
- Pistachio ice cream
- Heirloom tomatoes
- Fresh wild berries
- Foie gras
- Rice and beans
- Brawn, or head cheese
- Raw Scotch Bonnet pepper
- Dulce de leche
- Oysters
- Baklava
- Bagna cauda
- Wasabi peas
- Clam chowder in a sourdough bowl
- Salted lassi
- Sauerkraut
- Root beer float
- Cognac with a fat cigar
- Clotted cream tea
- Vodka jelly
- Gumbo
- Oxtail
- Curried goat
- Whole insects
- Phaal
- Goat’s milk
- Malt whisky from a bottle worth $120 or more
- Fugu
- Chicken tikka masala
- Eel
- Krispy Kreme original glazed doughnut
- Sea urchin
- Prickly pear
- Umeboshi
- Abalone
- Paneer
- McDonald’s Big Mac Meal
- Spaetzle
- Dirty gin martini
- Beer above 8% ABV
- Poutine
- Carob chips
- S’mores
- Sweetbreads
- Kaolin
- Currywurst
Durian- Frog’s Legs
- Beignets, churros, elephant ears or funnel cake
- Haggis
- Fried plantain
- Chitterlings or andouillette
- Gazpacho
- Caviar and blini
- Louche absinthe
- Gjetost or brunost
- Roadkill
- Baijiu
- Hostess Fruit Pie
- Snail
- Lapsang souchong
- Bellini
- Tom yum
- Eggs Benedict
- Pocky
- Tasting menu at a three-Michelin-star restaurant
- Kobe beef
- Hare
- Goulash
- Flowers
- Horse
- Criollo chocolate
- Spam
- Soft shell crab
- Rose harissa
- Catfish
- Mole poblano
- Bagel and lox
- Lobster Thermidor
- Polenta
- Jamaican Blue Mountain coffee
- Snake
(thanks to this generator and mordaxus at Emergent Chaos for the link.)
White Noise – An Electric Storm : 1969 album by David Vorhaus and Delia Derbyshire of the BBC Radiophonics Workshop: ‘one of the freakiest, most frightening, far out and forward thinking albums you may ever get to hear’
(tags: 1969 sixties music psych white-noise delia-derbyshire bbc radiophonics-workshop electronic)vim-flymake.vim : hooray! Flymake, on-the-fly compilation & error checking, for VIM. bit kludgy though, would be better if it integrated with vim 7.1’s “compiler” support
(tags: vim flymake compilers error-checking editors vi software)
non-PC devices increasing browser share : .5 – 1.5% of visitors to Warner music sites are now coming from games consoles and smartphones. bad news for Flash sites (via Torrez)
(tags: flash web browsers via:torrez warner-music os)full(4): always full device : ‘Writes to the /dev/full device will fail with an ENOSPC error. This can be used to test how a program handles disk-full errors.’ – that’s nifty. I can’t believe I’m still finding useful new UNIX features after 18 years
(tags: devices unix linux testing disks errors edge-cases enospc manual-pages)
2 Stage Transfer Drawing (advancing to a future state) on Vimeo : some great performance art from Irish artist Joan Healy; the installation appears to be a kiosk with a screen, and a touch pad. The pad itself is supposed to have a warm, soft, fleshy feel that ‘adds to the bond between people and machines’. However — in reality, it’s the artist’s back; she’s inside the kiosk, Mechanical Turk-style. Super-creepy
(tags: art creepy cool ireland joan-healy performance-art touchpads ui interface hci video)The Daily Show’s TiVo setup : cool details on how TDS captures the news networks’ TV output every day; they use TiVos, not MythTV. what they have works well enough, and that’s good enough for them (via Waxy)
(tags: mythtv tv the-daily-show tivo via:lhl)
Wow, this is pretty massive. The Irish Payment Services Organisation has again released details of a credit-card breach, this time on retail Point-of-Sale card terminals. Quoting the Irish Examiner story:
Una Dillon, head of card services at the Irish Payment Services Organisation, said the criminals went into the shops pretending to be doing maintenance work on behalf of the banks.
“We have discovered only in the last 48 hours that a number of retailers have been affected by a point-of-sale compromise,” she said. “We are in the lucky position that it was discovered quickly and the gardaí are working on it.
“Gardaí have uncovered a lot of the devices and CCTV footage. We have a list of all the card numbers that have been used. They have either been blocked or restrictions put on those cards.
“With the devices recovered it may just be that the cards were only saved and the criminals did not have a chance to get hold of the card numbers.”
“There will be an emergency meeting today with the gardaí, the terminal vendors and the banks to try and close down on this,” she said, adding the gardaí were in pursuit of the gang.
Insufficient authentication of maintainance staff is being blamed:
“The criminals have been going into shops claiming to be engineers working on the terminals. Staff are used to their bank officials coming to update terminals so unfortunately they have been able to do that.
Bank of Ireland estimated 3,100 of its debit and credit cards were affected and Ms Dillon said the other eight card providers could have similar numbers.
Bank of Ireland said, as a temporary measure, it had reduced the daily withdrawal limit on all its debit cards for ATM transactions outside Ireland to just €100 to protect customers from fraud.
They haven’t released the names of the affected shops yet; 20,000 cards, though, sounds like it’s been going on for while, on a large scale. Yikes.
The SiliconRepublic story claims that the gang ‘plugged in wireless devices that pushed the data to the internet and allowed the card numbers to be used overseas.’ However, in the past, these ‘wireless devices’ didn’t use the internet; instead they use parts from mobile phones, which relayed PINs, card numbers and CVV security codes via SMS text messages to Romania. That model seems more likely here, I would guess, due to the reliability of phone networks.
Update: last night’s RTE Six-One news bulletin (viewable as streaming RealVideo or transcoded 5MB AVI file), made it clear that the hardware used phone components and SMS. It had some pretty good pics of what appears to be a sample subverted POS terminal:



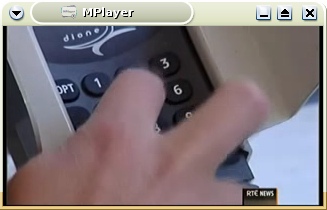


VISA have been warning about attacks on petrol-pump-based POS terminals since 2006, e.g. this story, but they’re more easy to attack since there’s few or no staff present by the pumps when the POS terminal subversion takes place. This has resulted in most petrol stations in Ireland disabling POS credit-card payment systems, requiring customers to pay at the counter; we lose convenience, but at least we’re probably not being skimmed. But these in-store POS terminals seem to be increasingly under attack; there are reports from Livigno, Italy, Rhode Island, and Canada.
The tamper-proofing of POS terminal hardware is unreliable; it’d be nice to see them made harder to tamper with. I would guess the gang used secondhand, hacked POS terminals, which supposedly should be tamper-evident (ie. easy to spot modifications).
Better yet, if Chip-and-PIN cards used end-to-end crypto between a crypto smartcard and the bank’s central systems, POS hacks would be impossible. But there’s no sign of that happening.
Most importantly, IPSO has promised that ‘banks will refund any customers whose details have been used to make fraudulent transactions.’ That’s key. It’s interesting to note that IPSO have been hammering home this point repeatedly in their stories — they’re worried about customer confidence, I’d guess.
The Evolution of Pre-Launch Gmail In Screenshots : fascinating! They really did a good job improving the UI, early revs were quite uninspiring
(tags: gmail google history email web ui)SealSkinz : waterproof socks and gloves — come recommended by Dublin’s cycle-couriers to avoid wet feet in all this bloody rain. lots and lots of good testimonials
(tags: dryness feet comfort clothing rain weather cycling outdoors socks gloves)
Emergent Chaos: Certifiably Silly : Adam Shostack tells the truth re Firefox 3’s stupid self-signed cert bug. ‘imposing yet another security tax, based on a static analysis of attackers and some certificate authority pixie dust, isn’t going to help things for very long.’
(tags: firefox firefox-3 security certificates ssl tls ca pki adam-shostack ui usability)Image Cerberus: a SpamAssassin plug-in against image spam : a new plugin, subject of a paper at this year’s CEAS conference it looks like
(tags: plugins spamassassin anti-spam image-spam images ceas conferences)Twitter drops SMS-notification support for EU users : interesting, I haven’t received the mail, and it claims to still be sending updates to my Irish mobile (update: I’m not actually *getting* any updates, though)
(tags: twitter phones mobile sms ireland eu uk)
A friend writes:
‘I switched my Vodafone bill to "online", to cut down on junk mail. When I tried to log in to view my bill, I was asked for a second level password, specifically:
"your password is the last 4 digits of your customer number (which appears at the top of your phone bill). "
So, I can’t see my phone bill because I can’t see my phone bill.’

The Trifecta of FAIL : ah, the hazards of monkey-patching core classes illustrated perfectly; a Ruby point-release upgrade broke Rails (via chromatic)
(tags: ruby rails monkeypatching ouch programming coding oo subclassing apis)best intranet form ever : ‘The software my employer uses for booking holidays has recently been “upgraded” and we now need to specify an absence reason.’ there are several hundred reasons, including ‘Abortion’, ‘Stroke’, ‘Warts’, ‘Dementia’, ‘Rectal Problems’, ‘Manic Depression’ and, um, ‘Wax’. best of all, this is for booking time off in advance…
(tags: intranet funny inept hr wtf daily-wtf bureaucracy pto holidays)Sup : ‘a console-based email client for people with a lot of email [..] The goal of Sup is to become the email client of choice for nerds everywhere.’ Looks like they’ve nicked a few ideas from GMail, too (via Luis)
(tags: via:tieguy console linux unix sup mail mail-readers ui apps)
Cycle Helmets and Other Religious Symbols : there appears to be a lack of published research suggesting that bike helmets help avoid serious injury and death — in fact, research seems to suggest the _opposite_.
(tags: cycling helmets safety research bikes equipment)Clever method of near duplicate detection : ‘SIGIR 2008 paper, “SpotSigs: Robust and Efficient Near Duplicate Detection in Large Web Collections”‘. may be useful, although we’ve pretty much stopped deduping in SpamAssassin nowadays
(tags: corpora dupes duplicates spotsigs collections sigir papers via:jzawodny)HadoopStreaming : ‘Using the streaming system you can develop working hadoop jobs with extremely limited knowldge of Java. [..] Hadoop basically becomes a system for making pipes from shell-scripting work (with some fudging) on a cluster.’
(tags: hadoop perl streams unix distcomp clusters mapreduce)political zealot using GMail’s “this is spam” button to deliberately cause spamfilter problems for Obama’s campaign : ‘Tablemate at benihana confided how he subscribes to Obama’s mailing list and marks it all as spam to train Gmail. Urge to kill rising.’ – Kevin Fox on Twitter
(tags: twitter kevin-fox foaf-story benihana obama anti-spam filtering this-is-spam us-politics moveon)“Jake Leg” : ‘large numbers of [adulterated Prohibition-era alcohol, Jamaican Ginger Extract] users began to lose use of their hands and feet. Some victims could walk, but they had no control over the muscles which would normally have enabled them to point their toes upward. Therefore, they would raise their feet high with the toes flopping downward, which would touch the pavement first followed by their heels. The toe first, heel second pattern made a distinctive “tap-click, tap-click” sound as they walked. This very peculiar gait became known as the jake walk and those afflicted were said to have jake leg’
(tags: jake-leg walking history prohibition alcohol odd bizarre adulteration poison 1930s)
Luis Villa, in a post to FoRK:
I have found that [mail] threading is overrated, in part because I’ve realized that any conversation so baroque as to actually require threading probably isn’t worth following.
Even though I wrote a threader for MH, I have to admit by now that he has a point ;)
An Illustrated Guide to the Kaminsky DNS Vulnerability : great guide to Dan’s most recent discovery. it really is quite nasty (via Jeremy)
(tags: via:jzawodny dan-kaminsky dns security exploits bind)
Noted on Twitter:
simonw: So apparently http://www.news.com.au/ used json-time for their Beijing countdown widget and blew my App Engine quota! They’ve stopped now.
uh, great. That’s useful.
Google — how are we supposed to host useful services with those limits?
Green Karma – Carbon-offset your colo box must-read post from Chris. If you run a colo box, you should think about offsetting the ~2 tonnes of CO2 output it generates per year
sorenragsdale: Building a Cheap ZFS Server good set of details on MrN’s new ZFS-based home disk server
Malwebolence – The World of Web Trolling holy crap, those /b/tards are fucked up
TechCrunch UK campaigning for a “Digital Hub” I have to say, the Digital Hub is actually a great place to work; it’s well worth duplicating, if such a thing is possible
419eater anti-scammers fool 419ers into performing the Dead Parrot sketch “Possibly, he is pining for the fee-ords”
Google taking action against Nigerian/419 fraud spammers Good news. About time, too ;)
Del.icio.us 2.0 goes live yay! I’ve been waiting for this for yonks
10 years of Boards.ie massive ~50GB RDF/XML dump, for open crunching, to generate interesting “SIOC Semantic Web” apps
Postmaster.comcast.net how to get mail delivered successfully to Comcast, the usual stuff
Why we’ll never replace SMTP ‘The reason that e-mail is uniquely useful is that you can exchange mail with people you don’t already know. The reason that spam exists is that you can exchange mail with people you don’t already know.’ +1
“Bikes-for-Billboards” scheme exposes major planning flaws ‘what was initially hailed as “free bikes” has become one of the biggest planning controversies to hit Dublin in years.’ No shit. 70% of sites are on the Northside, rather than the richer Southside; and each bike will cost over EUR300k in ad revenue!
Rob Enderle’s page on Wikipedia detailing this analyst’s hilariously wrong pro-SCO, anti-Apple/Linux predictions over the years. John Gruber: ‘the only way it would be worthwhile for reporters to [quote him] would be if they were willing to describe him as “almost always utterly wrong”‘
soc.culture.irish on “Cuil” meaning knowledge ‘eagerness, fearsomeness, a gnat, a horsefly, a beetle, a bluebottle, and (with the addition of a fada) a rear end, a reserve or backup, a corner, and an arse. The one thing it isn’t, according to the four dictionaries I just checked, is knowledge.’
I’m back from a week in Cornwall. I’d like to say I was rested, but chasing after an 11-month-old baby in a caravan isn’t all that restful. Still, it was sunny, and good for a change of pace ;)
Via b1ff.org, here’s the Nexis search that US Department of Justice White House liaisons ran on job candidates to determine their political leanings:
[first name of a candidate] and pre/2 [last name of a candidate] w/7 bush or gore or republican! or democrat! or charg! or accus! or criticiz! or blam! or defend! or iran contra or clinton or spotted owl or florida recount or sex! or controvers! or racis! or fraud! or investigat! or bankrupt! or layoff! or downsiz! or PNTR or NAFTA or outsourc! or indict! or enron or kerry or iraq or wmd! or arrest! or intox! or fired or sex! or racis! or intox! or slur! or arrest! or fired or controvers! or abortion! or gay! or homosexual! or gun! or firearm!
This Nexis reference says the "w/n" keyword searches for ‘words .. within 5 or 10 words of each other, Ex: "Enron w/5 investigation"’.
This is just a smidgen away from the concept of a SpamAssassin-style scoring filter. Crazy stuff.
Best of all, it’s buggy and over-sensitive, according to one librarian: ‘If that is really their search string, they were going through 99% unrelated citations. There need to be a very nested set of parentheses to make the terms work, starting with one after the w/7. Fired and sex are OR’ed twice and need to be nested, at least in the case of Fired and the OR’d terms immeadiately following.’
Update: good Slashdot comment thread here. This comment indicates that the above librarian might be off-base regarding the w/7 parentheses, since the OR operator has higher priority. Here is an even better walkthrough of the query statement logic. Finally, here’s an explanation of the "spotted owl" curiosity…
Why Spam Can’t Be Stopped – Emailappenders And Others Sell Bogus Lists Marketing company buys list of addresses, 85% of the 100k addresses bounce, marketer gets booted by ISP for spamming, marketer issues complaining press release. Let’s say it again: opt-in permission can’t be sold, and address list vendors are spammers
ZSFA — I Want The Mutt Of Feed Readers Zed recommends Newsbeuter. must take a look
We Want A Dead Simple Web Tablet For $200. Help Us Build It. having worked on a project to do just this, believe me, this is doomed. DOOMED
Science Clouds ‘compute cycles in the cloud for scientific communities .. allows you to provision customized compute nodes .. that you have full control over using a leasing model based on the Amazon’s EC2 service.’ Wonder if they’d like to give SA some time ;)
O2 Leaking Customer Photos (updated) the JBoss/Tomcat install leaks the “secret” URLs through it’s default status page. this is the 3rd helping of FAIL for O2’s web team; 2 previous occasions in the last year exposed customer data through “secret” URL manipulation
Avant Window Navigator “a ‘dock-like’ (cough) navigator bar for the Linux desktop” (via Danny, again!)
trickle ‘user-space bandwidth shaper’, ie. like nice(1) for network bandwidth (via Danny)
RFC 5218 – What Makes For a Successful Protocol? ‘Based on case studies, this document identifies some of the factors influencing success and failure of protocol designs.’ (via spicylinks)
trickle ‘user-space bandwidth shaper’, ie. like nice(1) for network bandwidth (via Danny)
RFC 5218 – What Makes For a Successful Protocol? ‘Based on case studies, this document identifies some of the factors influencing success and failure of protocol designs.’ (via spicylinks)
-
ooer missus (via Kenneth)
Here’s an interesting form of advance fee fraud I hadn’t heard of before; it’s a good example of 419 scammers ruining yet another casual online marketplace.
Let’s say you have a room you want to rent. You put up a "housemate wanted" ad on Craigslist or wherever. Here’s the the reply you’ll get:
Hi There,
How re you doing? I hope all is well. I’m martha Robot , am 26 yrs old and Am originally from chester united Kingdom . Graduate of I have a master degree in fashion design and I work as a professional fashion designer. I’m am not in the united kingdom right now, i am presently in West africa . I am currently working on contract for a company call (African Family Home Fashions) here in West Africa which the contract will be ending soon. I will be returning to your place soon. I enjoy traveling, It is very interesting to get more knowledge about the new countries, new people and traditions. It’s great to have such a possibility. As i was searching through the web i saw the advert of your place . I would like to know maybe it’s still available becasue i’m extremely interested in it. Here are the questions i would like to know about the room before planing to move in to the following questions below:
A}I will like to know the major intersection nearest your neighbourhood.like shopping mall,Churches,bus line e.t.c
B}I will like to know the total cost for the my initial move as in first month rent and if you accept deposit.
C}I will like to know if there is any garage or parking space cos I will have my own car come over.
D}I will like to have the rent fee per month plus the utilities.
E}I will like to have the description of the place, size, and the equipments in there.
F}I will also like to know Your payment mode.
G}I will like to know if I can make an advance payment ahead my arrival that will be stand as a kind of commitment that I am truely coming over and for you to hold the place down for me.
I will be very glad to have all this questions answered with out leaving a stone unturned…You can Call my Landlord for more references in UK ..+447024046815.
Email me back:
Thanks. Martha.
Needless to say, this is a scam. Here’s how it works (courtesy of this post): The interested "applicant" will send a cashier’s check or money order for the deposit, the value of which greatly exceeds the actual amount requested. They will then claim the overpayment to be an honest error based on their confusion about how these things work, and ask the victim to send back a money order refunding that amount, or to send it on to a "travel agent" who is supposedly booking the scammer’s flight. The payment will be made via a non-refundable mechanism like the 419er’s favourite, Western Union. It will be a matter of great urgency, as they will claim to need the funds to make the trip over. Her money order will clear, their’s will not — and there’s no way to refund the payment, so it’s gone. This is a classic advance-fee fraud trick, it seems.
Got to love that nom de plume, though — "Martha Robot". GREE-TINGS MAR-THA RO-BOT!
Googling for ‘major intersection nearest your neighbourhood’ churches bus finds plenty more:
-
‘Melina Crawford, am 26 yrs old and Am originally from Sevilla, Spain‘
-
‘sanyo rose, am 28 yrs old and Am originally from Barcelona, Spain‘
-
Another ‘sanyo rose, am 28 yrs old and Am originally from Barcelona, Spain‘
-
‘a warning about Cassandra Sanchez, am 26 yrs old and Am originally from Barcelona, Spain‘
-
‘Dawn Louise Jamison, presently in Amsterdam Holland on a business trip‘
-
‘daniella Pedro, am 26 yrs old and Am originally from Barcelona, Spain‘
Finally, a Washington-based realtor has written up a good walkthrough of the scam. He notes:
I recently ran an ad on craigslist.com to see if they were still working it. Craigslist has posted many warnings against responding to such solicitations and I was curious if the scammers had moved on to more fertile ground. They have not; I received 16 such inquiries in one day to a simple ad offering a room for rent in Bellevue. I used a fictitious identity and a newly created email address. I’ll use the emails from just one of them as an example. This particular scammer managed to have a check on my doorstep by the next day!
(thanks to nimbus9 for the headsup)
-
new cinema listings site for Ireland. nice web2.0-ish layout, but missing lots of stuff you’d expect nowadays: search-by-reviews, feeds, Upcoming.org-style social features, etc. (in fact, they’d almost be better off just using Upcoming.org IMO ;)
-
paraphrased: “enough linkblogging! new content please!”
-
the bug appears to affect client-side resolvers, which can be cache-poisoned by malicious DNS servers using predictable TXIDs in DNS responses. current fix is to randomize ports when making queries? I think. more: http://www.kb.cert.org/vuls/id/800113
-
good guide to diagnosing I/O bottlenecks on modern Linuxes using -d and -x
-
no mention of what it does with mail from and so on, however (via Nelson)
-
‘a flexible, efficient, automated mechanism for serializing structured data – think XML, but smaller, faster, and simpler’, defined with an IDL-style language. see also Thrift and http://teddziuba.com/2008/07/build-google-protocol-buffers.html
-
by the Dutch team behind the crack of the Dutch travel card, based on the same MIFARE system as London’s Oyster cards. paper coming in October
-
Ryanair vs Bravofly, Bravofly scraping Ryanair’s site allegedly in contravention of their T&Cs
-
I’m quoted!, arguing that the death of invention in the modern age is greatly exaggerated: ‘the next Wikipedia could easily come from one teenager’s laptop in their back bedroom in Kildare […] the barriers to [invention] are lower than ever.’
-
‘The way things are going, I half-expect to hear a quiet electric “peep” noise each time I flush the toilet; another bowel movement logged by Bumland Security.’
-
as usual, a description of what you _shouldn’t_ be doing, provides a great illustration of what you _should_ be doing ;) (via Vinoski)
-
‘Four resourceful humans test the tolerance levels of four human resource managers by constantly failing to show up for work after being offered a job. The aim… To see who can hold onto their job the longest without ever working a day.’ truly hilarious
-
fix is to use the kernel from Intrepid Ibex, for now
-
aha. this explains a long-running issue I’ve had on my Thinkpad at home
-
‘a new text markup format. Its syntax is a blend of Donald Knuth’s TEX and various wiki markup.’ has a formal grammar, rather than an ad-hoc parser (guilty). quite nice, although would have been better if it didn’t reinvent so many wheels (via adulau)
-
[the Viacom/Youtube privacy disaster demonstrates] ‘what’s wrong with trusting corporations with your data: if the corporation says “I’m not going to be evil,” and the government says “oh yes you are,” it’s pretty much _the end of the conversation_.’
-
alt microblogging platform with a few key wins over Twitter & Jaiku: stability (so far!), open, decentralized, and Affero-licensed OSS. I’m “jm” on it, but not writing there — yet. but looking forward to an API so I can add it to twit.ie
-
some third-party app developers get access to it, some don’t. one dev says: ‘It’s frustrating to just get locked out after spending so much time making stuff for Twitter users’
-
910-node cluster sorting 1TB of data in 209 seconds, using Hadoop and HDFS. I wish we had a Hadoop cluster to do SpamAssassin mass-checks on ;)
-
‘a fast, distributed, in-memory workqueue service’, written in C with libevent, lots of client libs for different languages. Nice lifecycle model. The queues are not persistent yet, though, unfortunately
-
‘a semi-automated, largely passive web application security audit tool. .. detection and annotation of potential problems based on the observation of existing, user-initiated traffic in complex web 2.0 environments’, by lcamtuf
-
Bebo need to do some anti-abuse work
Over the past few weeks, I’ve increasingly heard of spam and abuse problems originating in Amazon EC2.
This has culminated in a blog post yesterday by Brian Krebs at the Washington Post:
It took me by surprise this weekend to discover that that mounds of porn spam and junk e-mail laced with computer viruses are actively being blasted from digital real estate leased to [Amazon].
He goes on to discuss how EC2 space is now actively blocked by Outblaze, and has been listed by Spamhaus in their PBL list. A spokesperson for Amazon said:
"We have a clear acceptable use policy and whenever we have received a complaint of spam or malware coming through Amazon EC2, we have moved swiftly to strictly enforce the use policy by network isolating (or even terminating) any offending instances," Kinton said. She added that Amazon has since taken action against the EC2 systems hosting the [malware].
However as Seth Breidbart noted in the comments, ‘note that Amazon will terminate the instance. That means that the spammer just creates another instance, which gets a new IP address, and continues spamming.’ True enough — as described, instance termination simply isn’t good enough.
My recommendations:
-
as John Levine noted, it’s likely that Amazon need to treat EC2-originated traffic similarly to how an ISP treats their DSL pools — filtering outbound traffic for nastiness, in particular rate-limiting port 25/tcp connections on a per-customer basis, so that an instance run by (or infiltrated by) a spammer cannot produce massive quantities of spam before it is detected and cut off.
However, I’m not talking about blocking port 25/tcp outbound entirely. That’s not appropriate — an EC2 instance is analogous to a leased colo box in a server farm, and not being able to send mail from our instances would really suck for EC2 users (like myself and my employers).
-
It would help if there were a way to look up customer IDs from the IP address of the EC2 nodes they’re using — either via WHOIS or through rDNS. Even an opaque customer ID string would allow anti-abuse teams to correlate a single customer’s activity as they cycle through EC2 instances. This would allow those teams to deal with the reputation of Amazon’s customers, instead of Amazon’s own rep, analogous to how "traditional" hosters use SWIP to publicize their reassignments of IPs between their customers.
There’s some more discussion buried in a load of knee-jerking on the NANOG thread. Here’s a few good snippets:
Jon Lewis: ‘I got the impression the only thing Amazon considers abuse is use of their servers and not paying the bill. If you’re a paying customer, you can do whatever you like.’ (ouch.)
Ken Simpson: ‘IMHO, Amazon will eventually be forced to bifurcate their EC2 IP space into a section that is for "newbies" and a section for established customers. The newbie space will be widely black-listed, but will also have a lower rate of abuse complaint enforcement. The only scalable way to deal with a system like EC2 is to provide clear demarcations of where the crap is likely to originate from.’
Bill Herrin: ‘From an address-reputation perspective EC2 is no different than, say, China. Connections from China start life much closer to my filtering threshold that connections from Europe because a far lower percentage of the connections from China are legitimate. EC2 will get the same treatment.’
There’s also an earlier thread here.
Anyway, this issue is on fire — Amazon need to get the finger out and deal with it quickly and effectively, before EC2 does start to run into widespread blocks. I’m already planning migration of our mail-sending components off of EC2; we’re already seeing blocks of mail sent from it, and it’s looking likely that these will increase. :(
(It’s worth noting that a block of EC2’s netblocks today will produce a load of false positives, mainly on transactional mail, if you’re contemplating it. So I wouldn’t recommend it. But a lot of sites are willing to accept a few FPs, it seems.)
Twitter has this nasty habit — if you come across a tweet in your feed reader containing a URL, and you want to follow that link, you can’t, because Twitter doesn’t auto-link URLs in its RSS feeds. Instead, you have to click on the feed item, itself, wait for that to open in the browser, then click on the link in the new browser tab. That link will, in turn, open in another new tab.
Here’s a quick-hack Greasemonkey user script to inhibit this second new-tab: